Security Management

Information Security Management Principles Trainosys

Protect Your Enterprise Analyze Your Security With Architecture Models
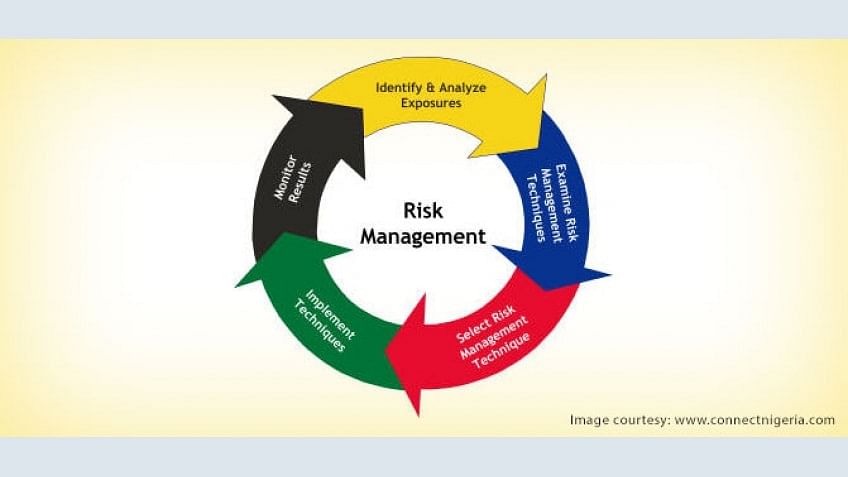
Cyber Security Security Risk Management Simplilearn Com

Overview

Information Security Management Model Download Scientific Diagram
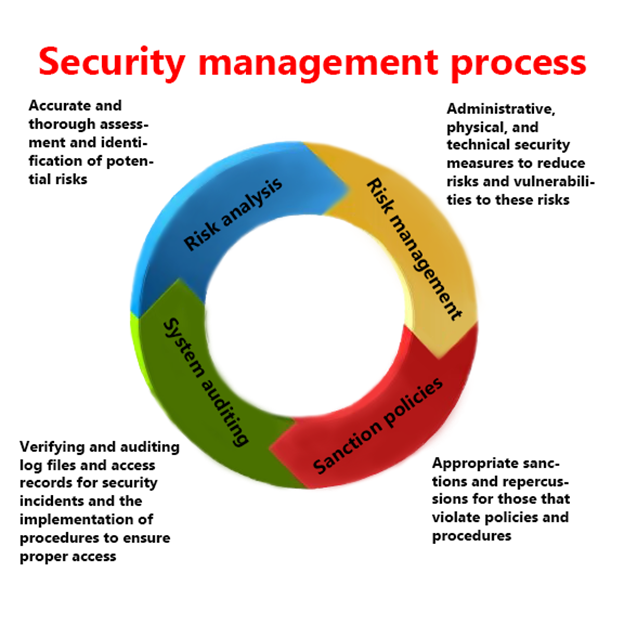
Cyber Security Starts Here The Security Management Process Jarvis Labs Official Site


Information Security Management Model Download Scientific Diagram

Implementing An Effective Cyber Security Management Plan Safety4sea

Iso Information Security Management Advanced Safety Consultancy

Cyber Security Management Plan Sqe Marine
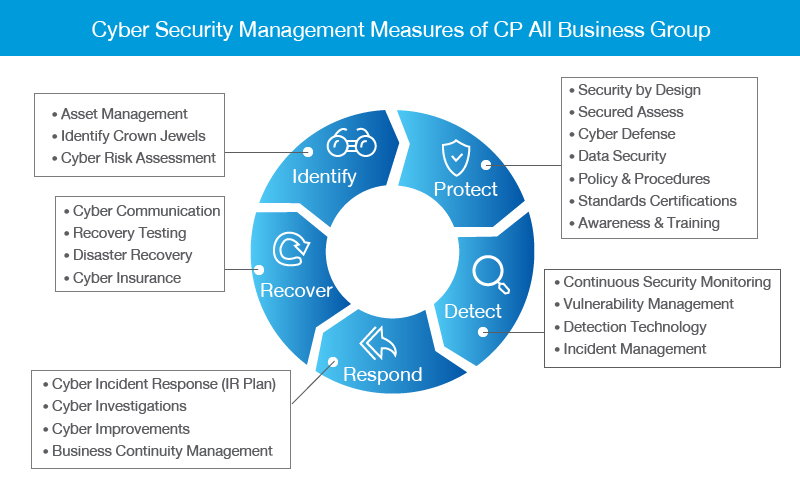
Information Security Cybersecurity System Availability บร ษ ท ซ พ ออลล จ าก ด มหาชน

Security Management Rahi Ireland

Retina 651 Security Management Appliance E Spin Group

Security Management Text 2903 1484 Transprent Png Free Download Text Technology Organization Cleanpng Kisspng

Business Analytics And Cyber Security Management In Organizations Ebook By Rakuten Kobo Singapore

Iso Iec Information Security Management System Dnv Gl
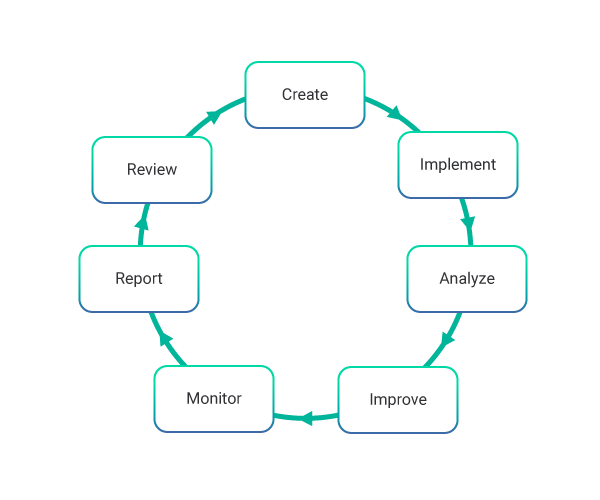
An Overview Of Information Security Management In Itil Invensis Learning

Compliance Audit For System Information Security Management System In Dwarka New Delhi Accredium Global Compliance Services Llp Id

Diploma In Security Management Temasek Polytechnic
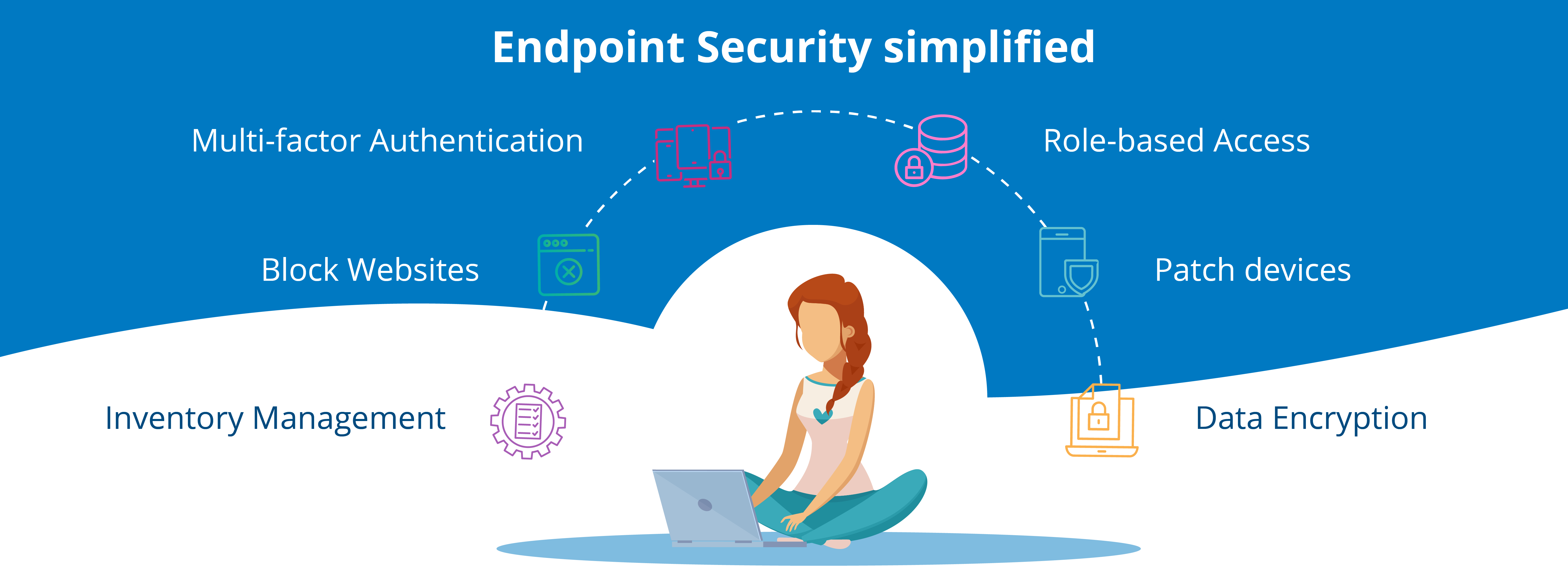
What Is Endpoint Security Endpoint Security Software Solutions Manageengine Desktop Central

Books Kinokuniya Effective Security Management 6th Sennewald Charles A Baillie Curtis

Iata Security Management System Manual
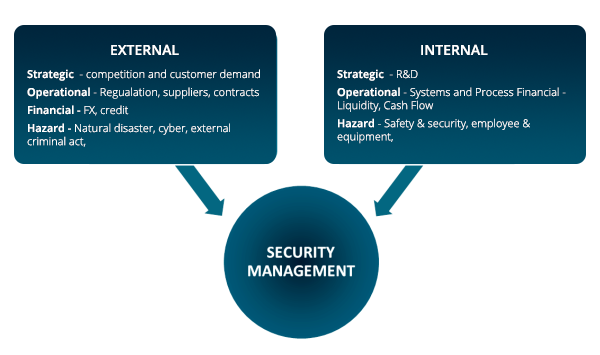
Security Management Sigma
1

Unified Security Management Systems Singapore

Security Management Systems Sems For Air Transport Iata
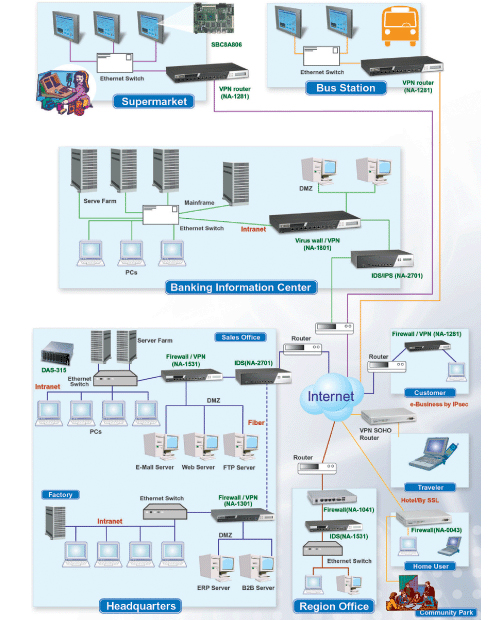
Network Security Management

Security Training Certified Corporate Security Management Specialist

Corporate Security Management Challenges Risks And Strategies Cabric Marko Amazon Sg Books

Chang Chang Security Management Pte Ltd Home Facebook

Network Security Management Process Street

What Is Information Security Management Ec Council
Idc Multidimensional Forces Drive Strong Growth China Operation And Maintenance Security Management Hardware Product Market Shares 19 Initial Release

Asset Inventory And Security Management In Ics Incibe Cert
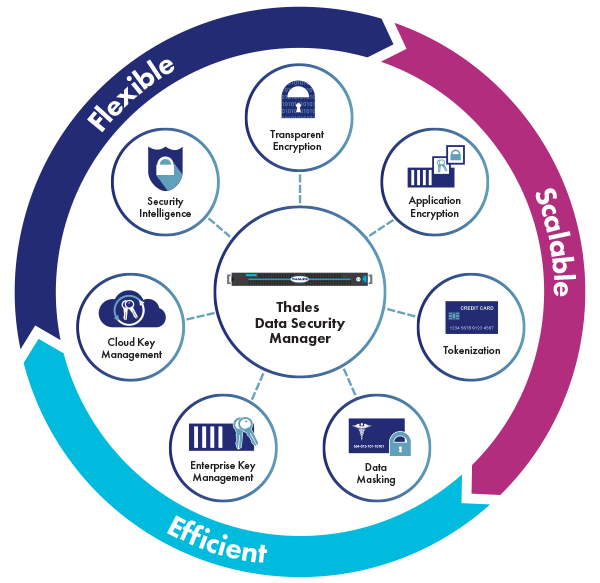
Vormetric Data Security Platform Thales

Professional Security Management A Strategic Guide 1st Edition Ch

Information Security And Personal Information Protection Csr Seven I Holdings Co

Iogp Report 512r Security Management System Processes And Concepts In Security Management Restricted To Iogp Members Iogp Publications Library

Royal Security Management Services Pte Ltd

Information Security Management System Netrika Singapore Security Risk Management Services Netrika Singapore

Hybridactive Cyber Security Management Services

Whistic Vendor Security Management Platform Product Review Sc Media
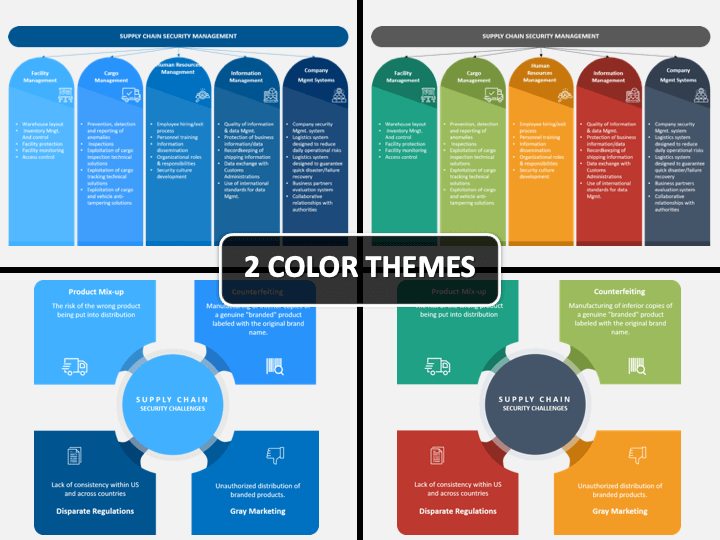
Supply Chain Security Management Powerpoint Template Sketchbubble

Security Management Partners Linkedin

How To Become An Information Security Manager Infosec Resources

It Security Management Mcon
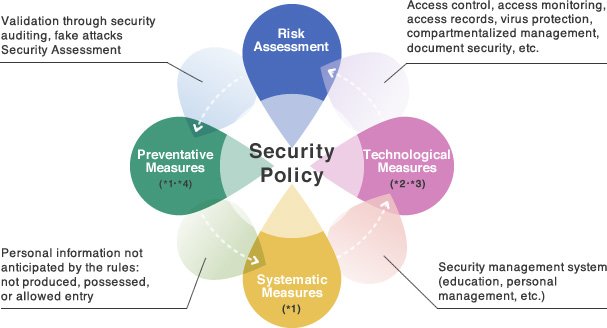
How To Implement Data Security Management System Webimprints Data Security Company

Supply Chain Security Management What Is It Definition Examples And More
Unified Security Management Usm Cybersecurity Excellence Awards
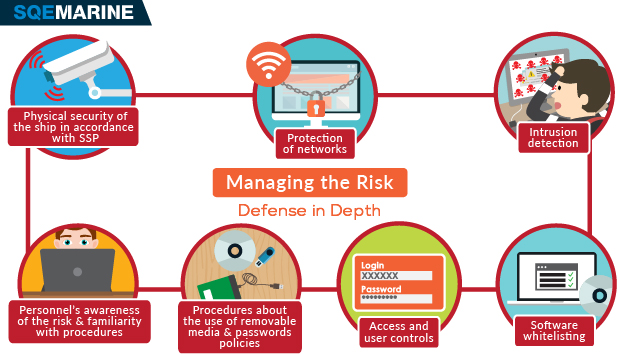
Implementing An Effective Cyber Security Management Plan Safety4sea
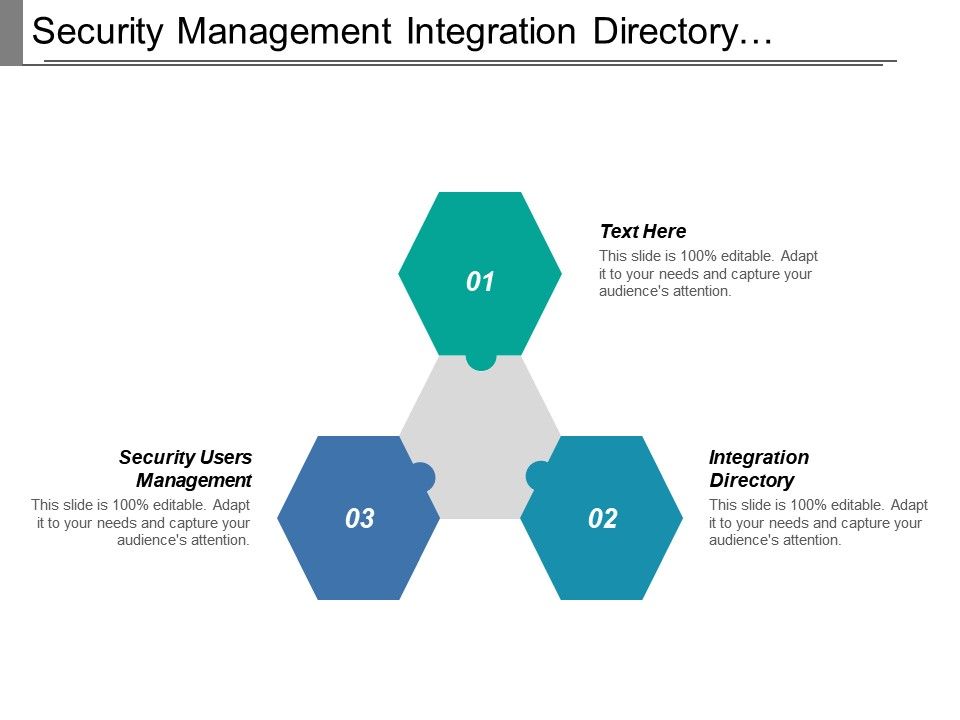
Security Management Integration Directory Process Composer Lifecycle Management Powerpoint Presentation Templates Ppt Template Themes Powerpoint Presentation Portfolio

Alpha Security Management Services Pte Ltd Facebook

Itil Version 3 Chapters
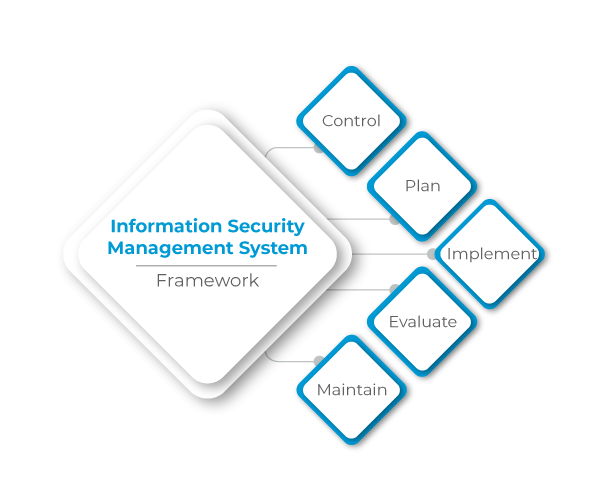
An Overview Of Information Security Management In Itil Invensis Learning

Algosec Security Management Solution Reviews Ratings Alternatives Gartner 21
Q Tbn And9gctyc Risl9s0mdlatlq Lvdlecq Sfjyboqpbqgn7jsp0eqc3eg Usqp Cau

Adnovum Security Consulting
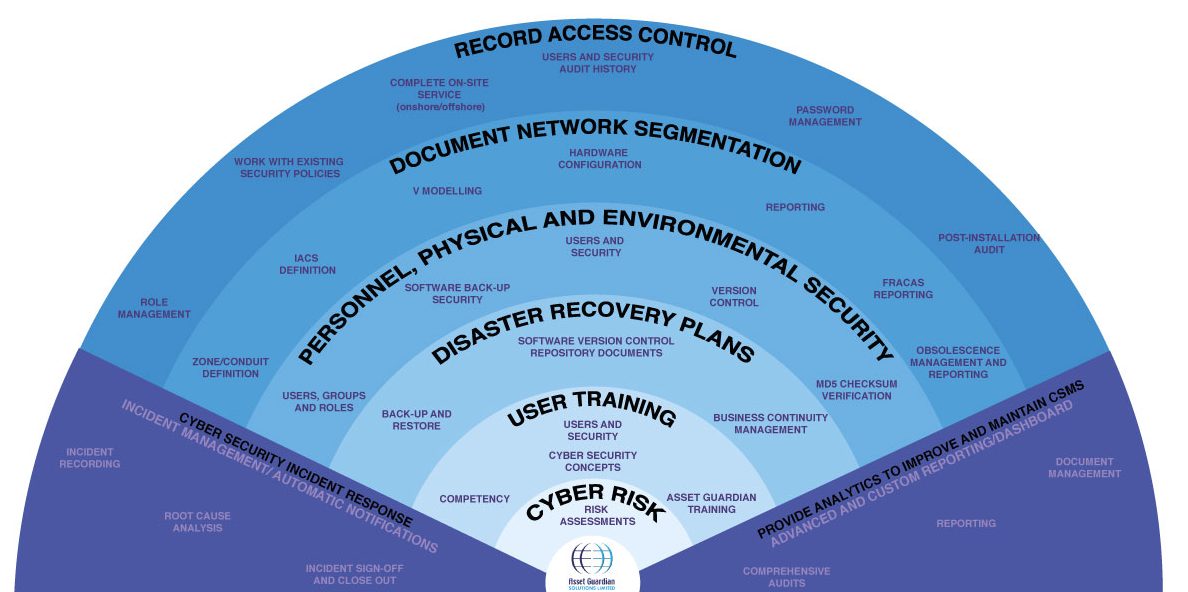
Cyber Security Management System Software Solution For One Of The World S Leading Oil And Gas Operators Asset Guardian Solutions Limited

E Guide 5 Steps To Achieve Risk Based Application Security Management

International Security Management Crime Prevention Institute Ismcpi Linkedin

Home Cyber Security Management
What Is Security Management In The Cloud Check Point Software

The 5 Things Your Information Security Management System Needs To Be Effective Insights Association
Q Tbn And9gcts9vp7bzr Jhsa5gygmkud987udyghypriulccreuznsghb Qc Usqp Cau

Security Management Training Consultant

Itil Information Security Management Itil Tutorial Itsm

The Information Security Management Cycle Download Scientific Diagram
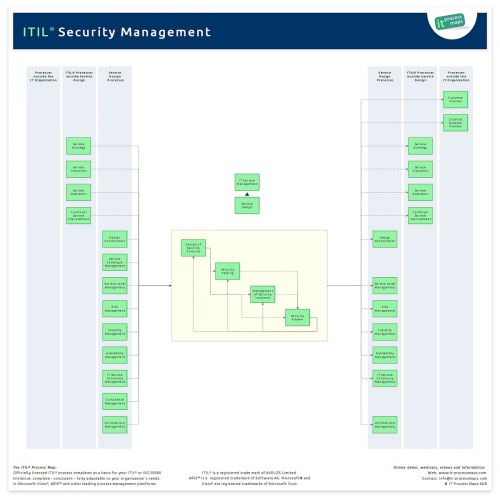
It Security Management It Process Wiki

End To End Security Management For The Iot Ericsson

Integrated Security Management Systems Isms Att Systems

Itil Version 3 Chapters
Q Tbn And9gcsvpfpllzbob4ziwugidwjldc8ygcjjxtjtz4ldk7xvhqaa531e Usqp Cau

Security And Risk Management Leaders Must Use Automation Gartner

Information Security Management System Fadamko
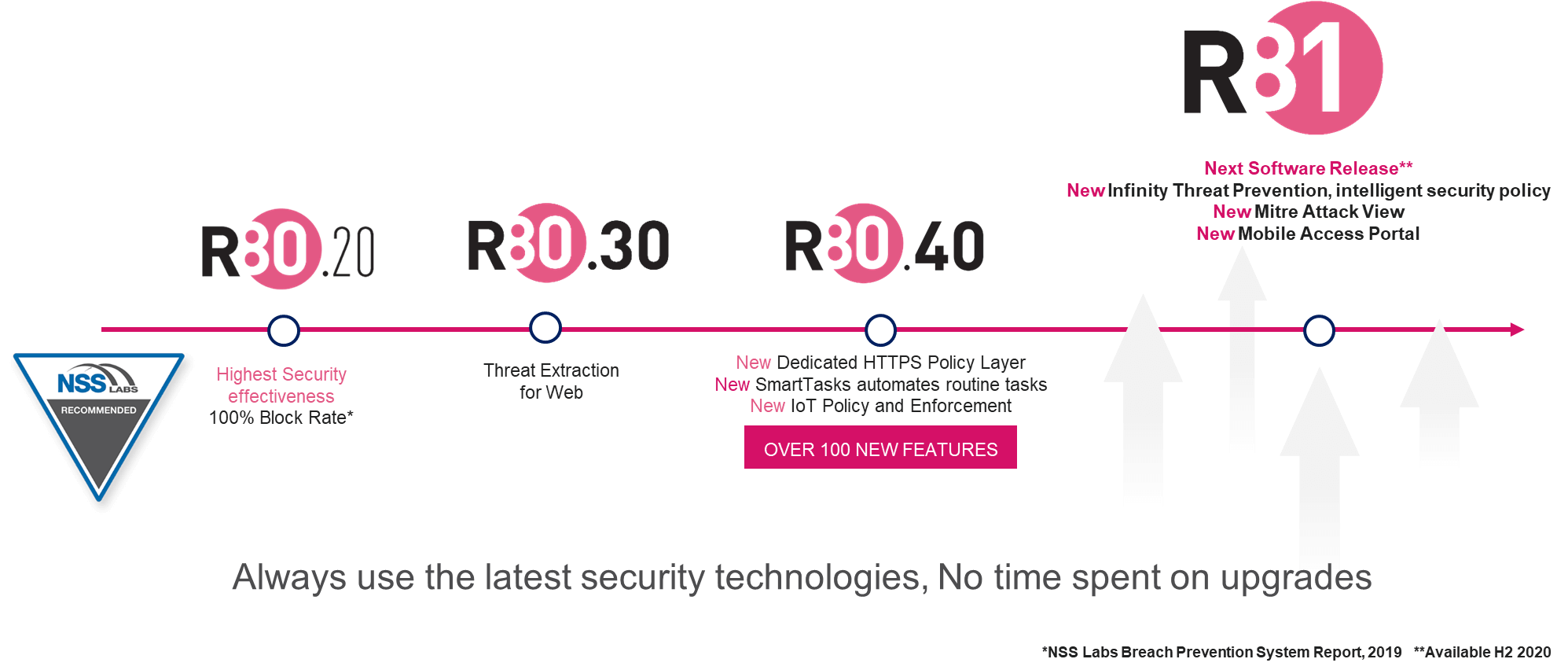
The Best Security Management Is Now In The Cloud Check Point Software

Risk Security Management Linkedin
Cyber Security Management Model Source Designed By The Authors Download Scientific Diagram

Iso Information Security Management Policy
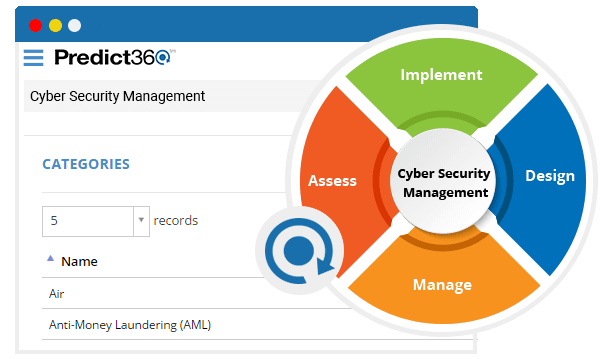
Cover Your Business Risks With Advanced Cyber Security Solutions 360factors

E Security
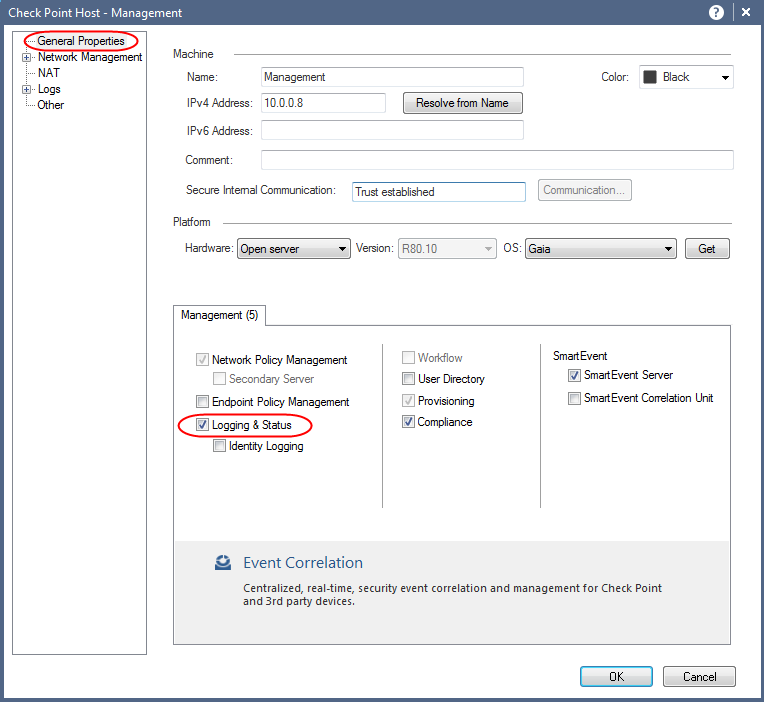
Best Practices Configuration Of Logging From Security Gateway To Security Management Server Log Server

Welcome To Algosec Security Management Suite

Alyne Cyber Security Governance Risk Management As A Service

Translation China S New Draft Data Security Management Measures
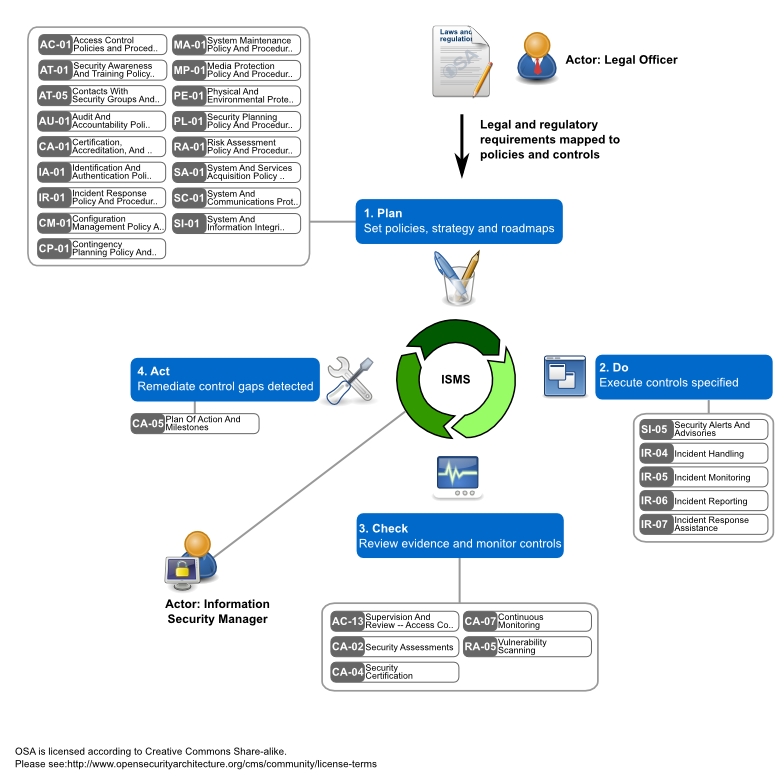
Sp 018 Information Security Management System Isms Module
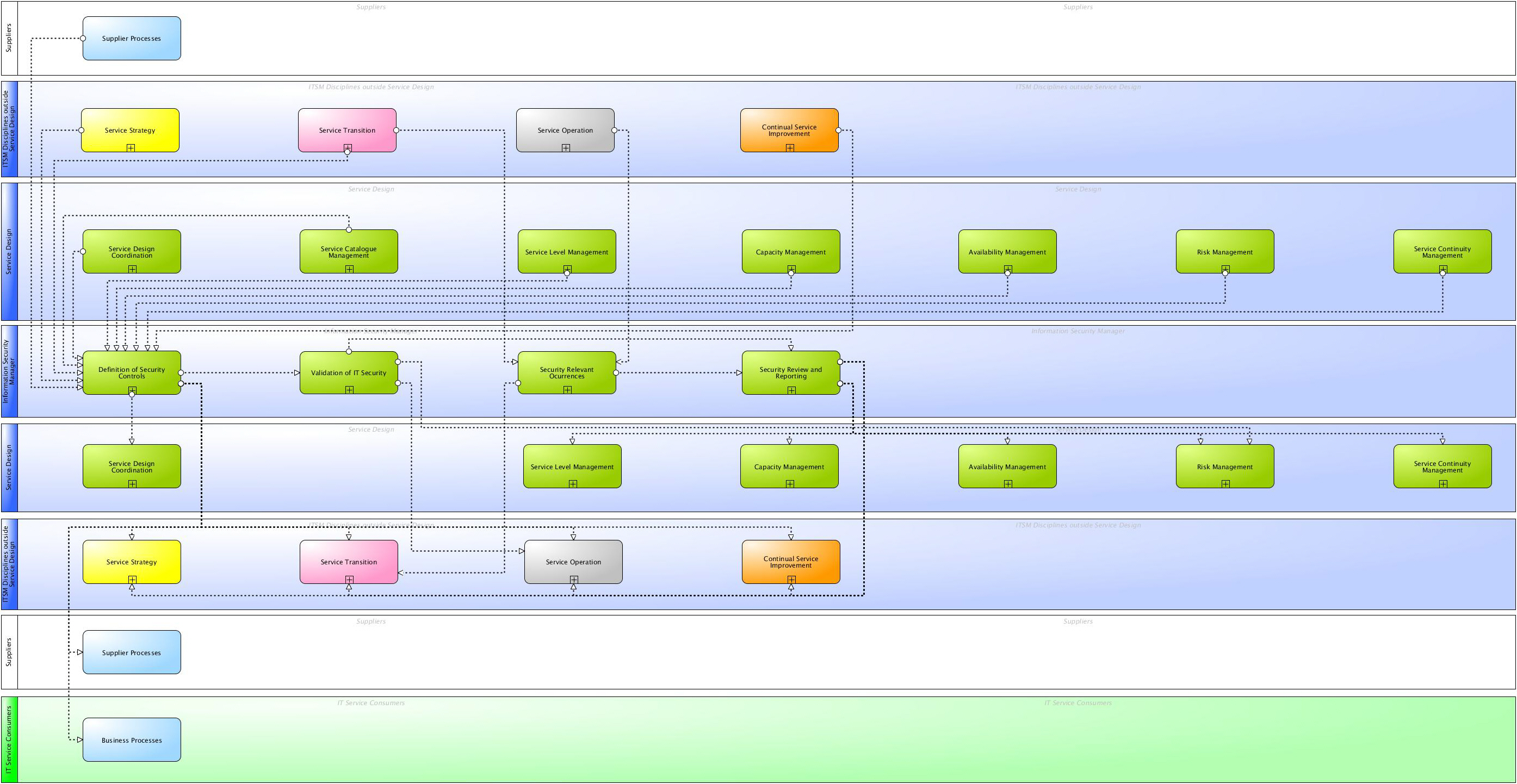
Itsm Wiki Processes Of Security Management
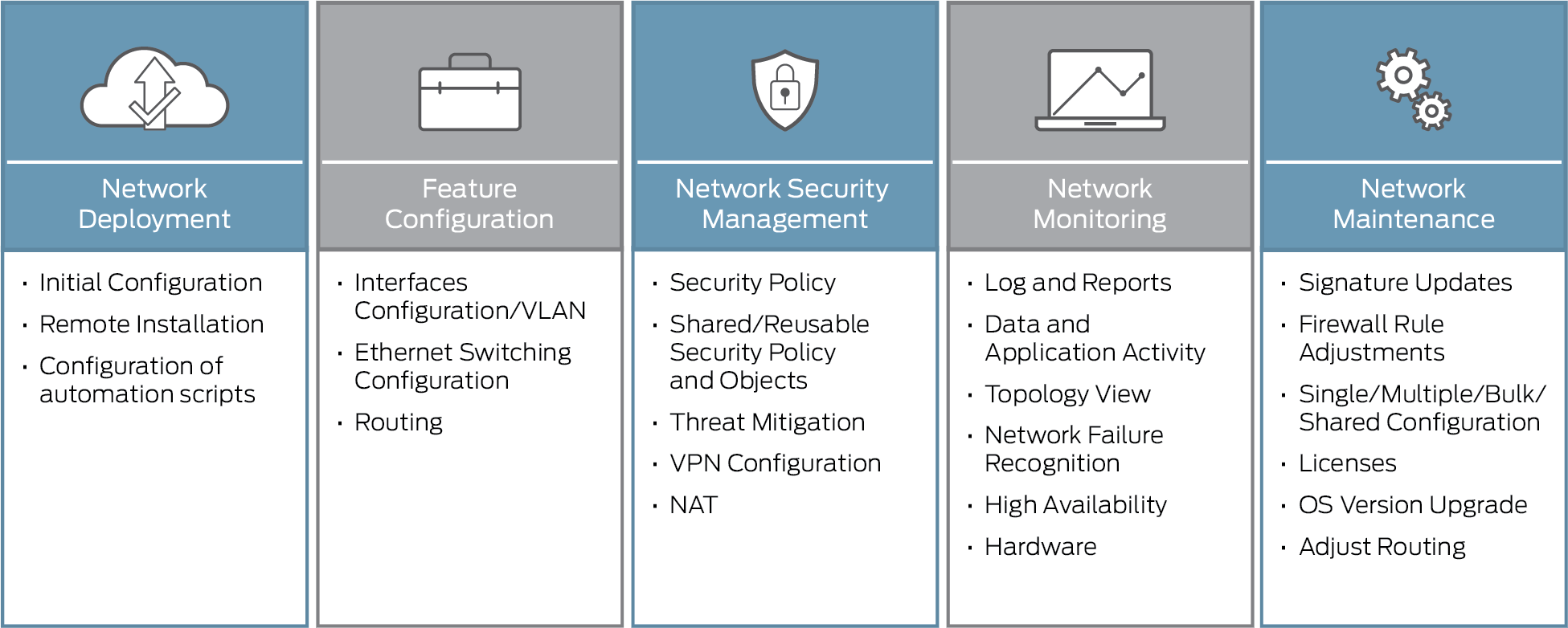
What Is Network Security Management Juniper Networks

How We Serve You Atvangarde

Mercury Security And Facilities Management Linkedin
What Is Security Management Architecture Check Point Software

Ascentiaa Security Management Pte Ltd Pindot Pte Ltd

Security Solutions Pristine Security Management Services Website

Iso Iec 13 Compliance Amazon Web Services Aws

Security Management My Blog

Gic Group Iso Iec Information Security Management System Gic Group
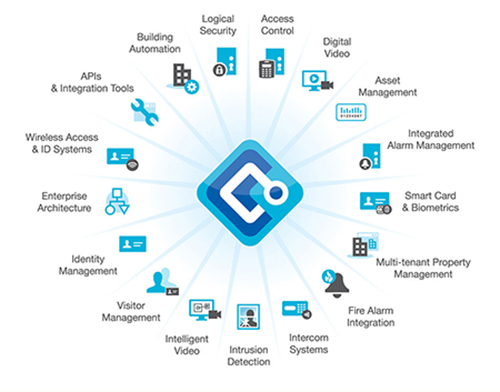
Total Security Management

Information Security Management System Isms Value Governance Research

Is It Time Your Business Adopted An Information Security Management System Nordea

Free Online Course International Security Management From Coursera Class Central

Security Management Overview

Information Security Management Professional Based On Iso Iec Exin

10 Best Practices For Network Security Management Observeit

Information Security Management System Isms Online

A Guide To Cloud Security Management



